Introduction to Computer Networking💻 :
Module 1: Basics of Networking 🚀
Overview of computer networks and their Significance ✨
Imagine you have a bunch of computers, smartphones, and other devices at your home. Now, think about how cool it would be if they could all talk to each other and share information easily. That's the basic idea behind computer networks. A computer network is a collection of devices (like computers, smartphones, and servers) that are connected so they can communicate, share resources, and work together.
Significance of Computer Networks: Computer networks are incredibly important for many reasons:
Sharing Resources: Networks allow devices to share resources like printers, files, and even processing power. For instance, in an office, multiple computers can use the same printer through a network.
Communication: They enable communication through emails, video calls, and instant messaging. When you send an email, it travels through a network to reach the recipient's device.
Information Access: Networks give us access to a world of information. When you search for something on the internet, your request goes through various networks to fetch the information and bring it back to you.
Remote Access: Networks let us access our files and data from anywhere. Cloud storage services like Google Drive and Dropbox use networks to let you get your files even when you're not at your computer.
Online Entertainment: Streaming movies, playing online games, and listening to music all rely on networks. When you watch a YouTube video, the data is sent to your device over a network.
Business and Collaboration: Companies use networks for sharing data among employees, video conferencing, and collaborating on projects. They can work together even if they're in different parts of the world.
E-commerce: When you buy something online, your order information travels through various networks to reach the seller's system, which then processes your order.
Social Media: Posting a photo on Instagram? It gets uploaded through a network to Instagram's servers so that your friends can see it.
So, computer networks are like digital highways that allow information and data to travel between devices and people all around the world. They make our connected, online lives possible and convenient!
Network types: LAN, WAN, MAN💻:
LAN (Local Area Network): Imagine you have a bunch of computers and devices at your home or within a small office building. If you connect them all together to share resources like printers, files, and an internet connection, you've created a Local Area Network, or LAN. It's like everyone in the same house sharing the same Wi-Fi network.
Example: A family with multiple laptops, smartphones, and a shared printer, all connected to the same Wi-Fi router, forms a LAN.
WAN (Wide Area Network): Now, let's think bigger. Imagine you have offices in different cities or even different countries. To connect all these offices and enable them to share information and resources, you use a Wide Area Network, or WAN. It's like connecting multiple LANs over long distances.
Example: A multinational company with offices in New York, London, and Tokyo uses a WAN to connect all their offices and share data seamlessly.
MAN (Metropolitan Area Network): If you want to cover an entire city with a network, you're looking at a Metropolitan Area Network, or MAN. It's larger than a LAN but smaller than a WAN. This could be used by institutions like universities or large organizations that have campuses spread across a city.
Example: A university with multiple campuses around a city connects them through a MAN to ensure students and faculty can access resources and communicate easily.
In summary:
LAN is for smaller spaces like homes and small offices.
MAN covers a whole city or a larger geographical area.
WAN connects multiple LANs or even MANs across long distances, possibly spanning cities or countries.
Network topologies: Bus, Star, Ring, Mesh 📜:
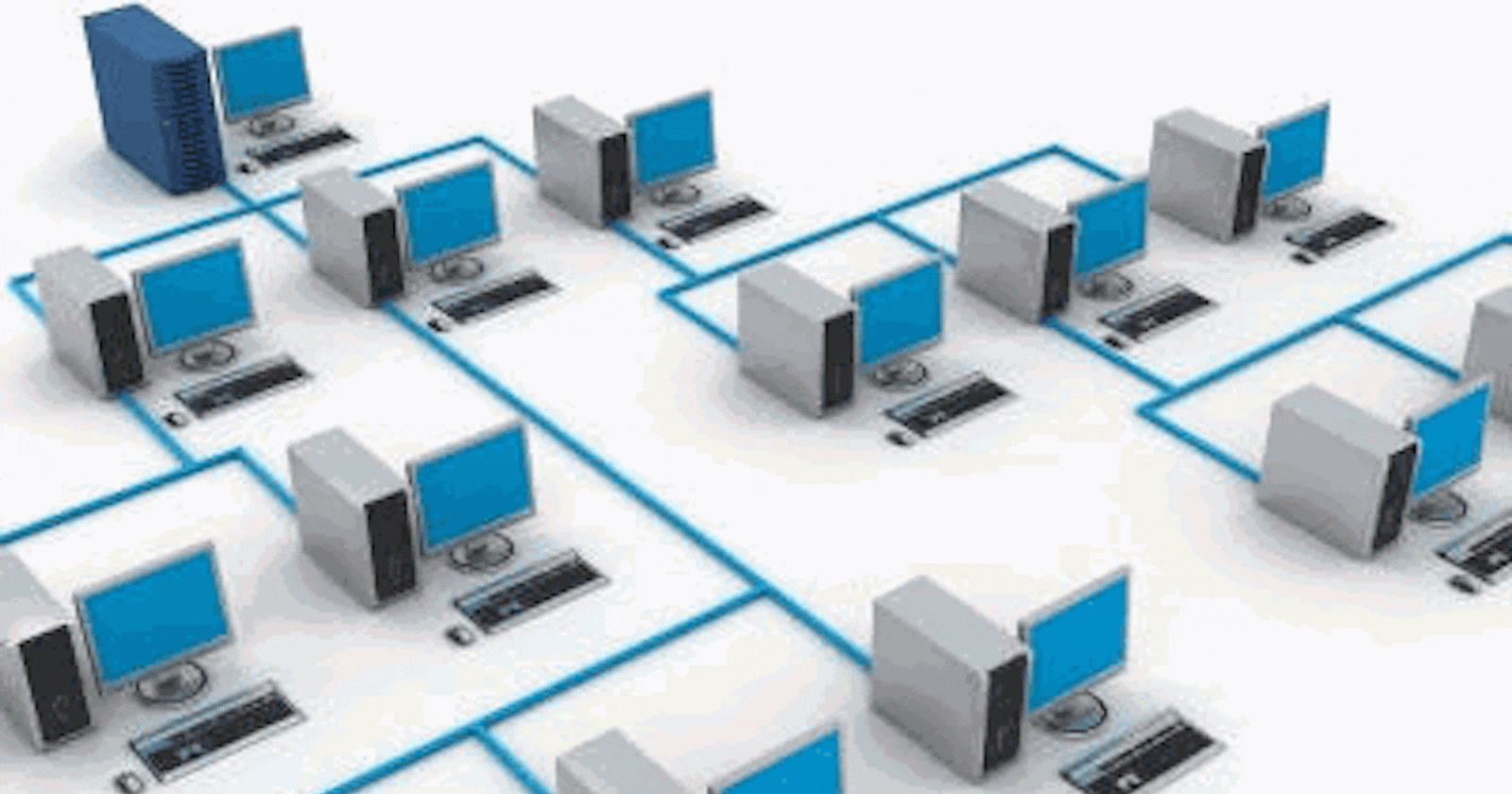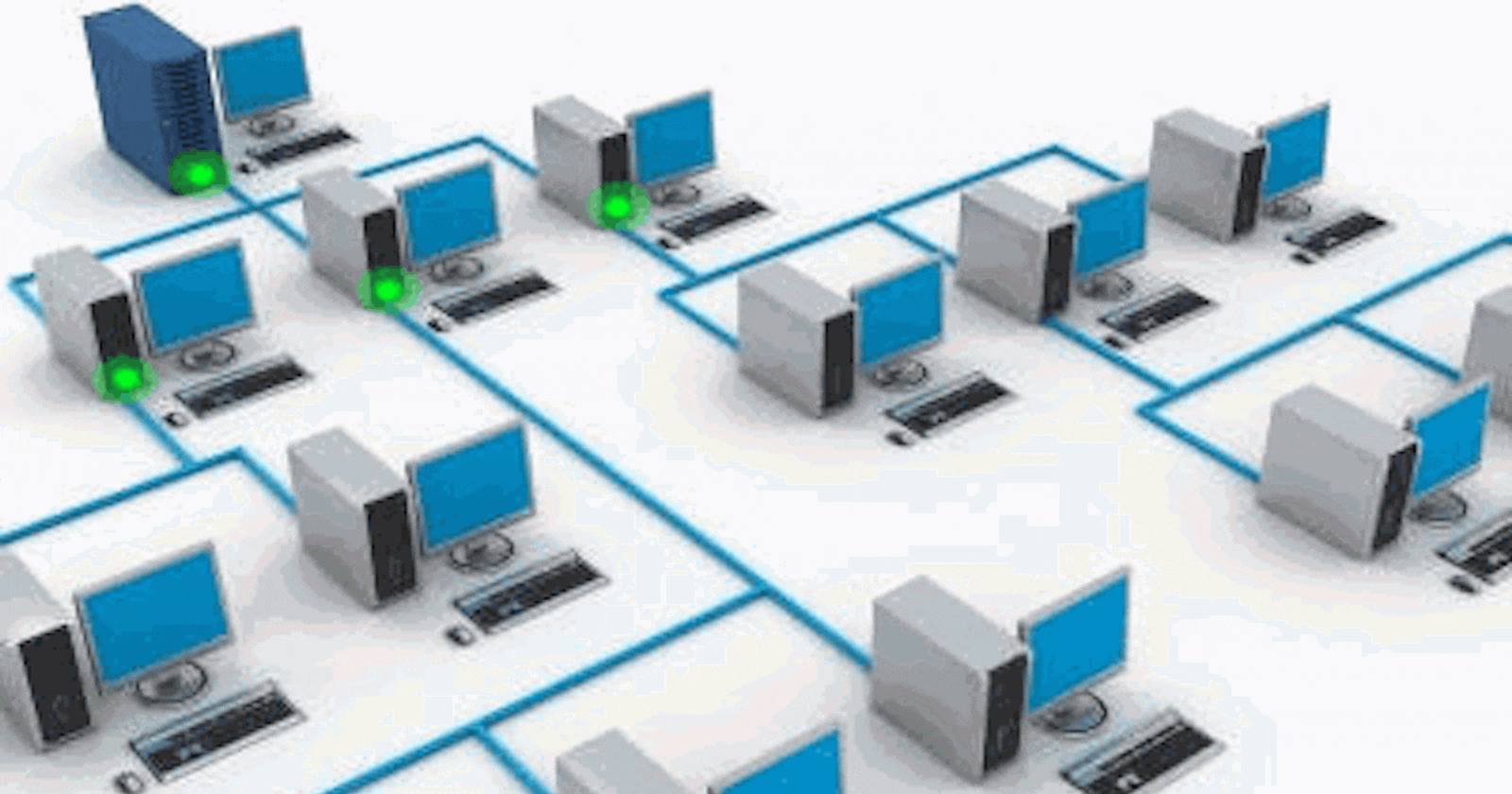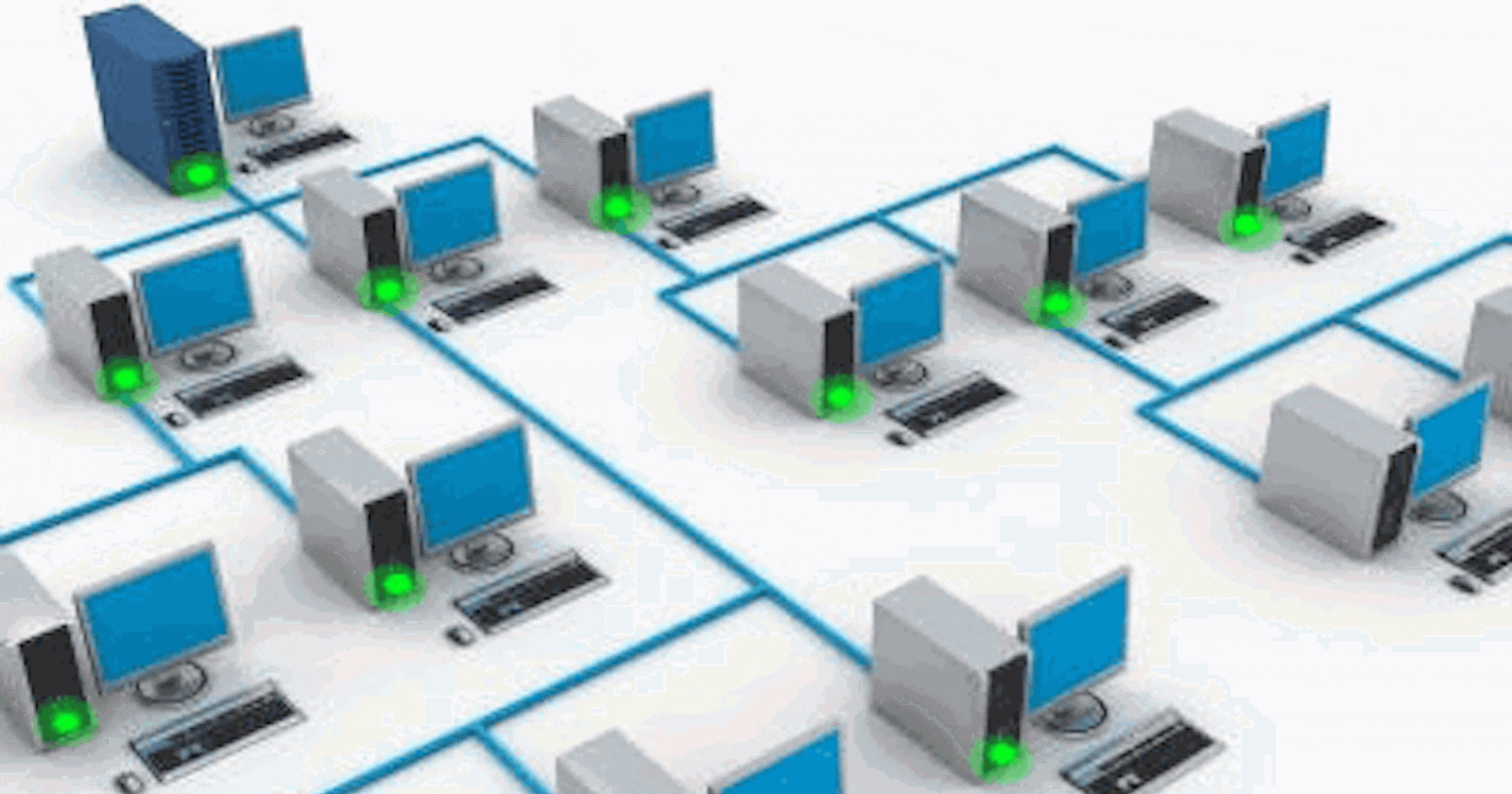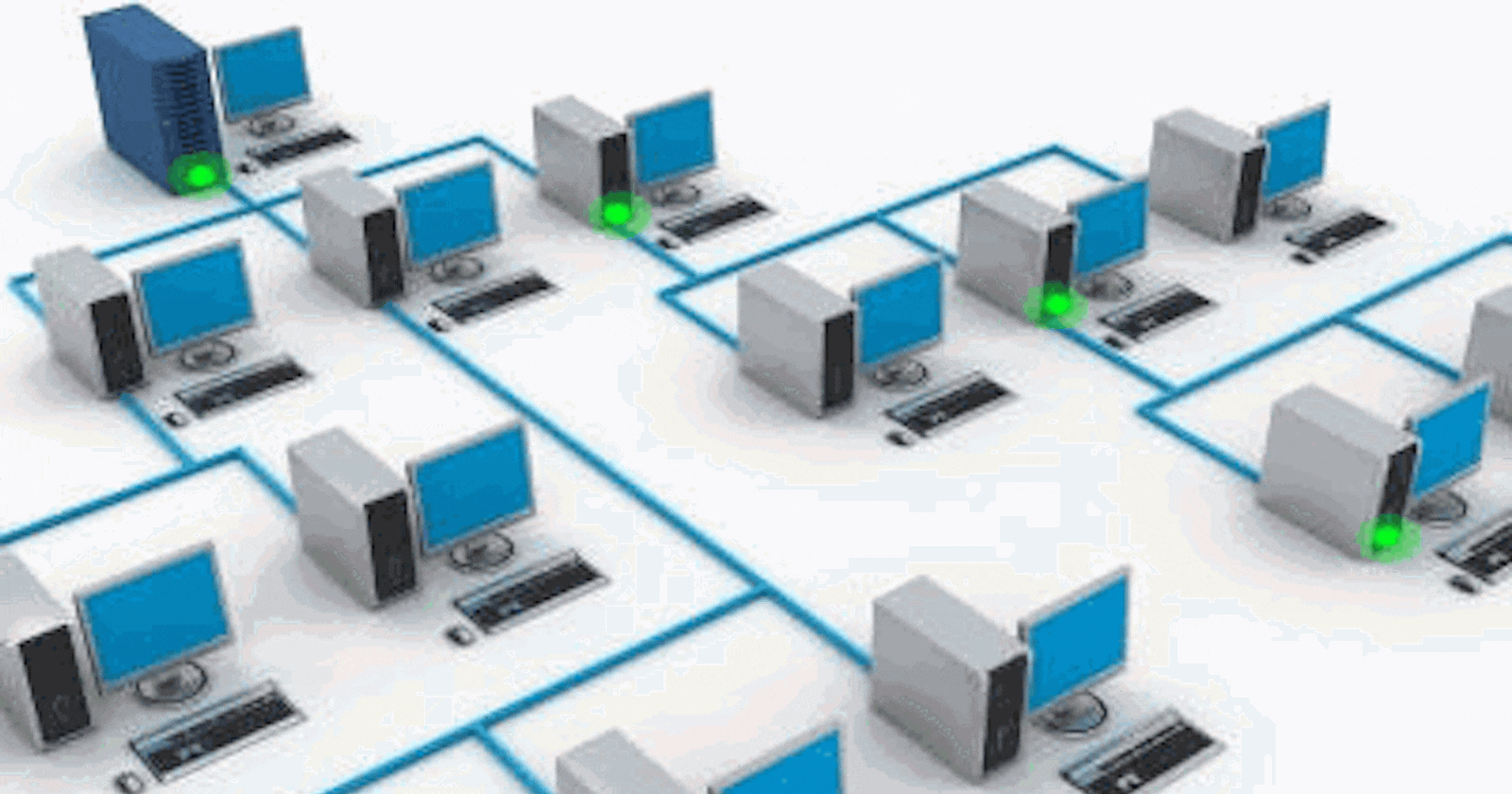
Bus Topology: Imagine a school classroom where all students are sitting in a single row. The teacher stands at one end of the row and communicates with the students by speaking aloud. In a bus topology, all devices (computers, printers, etc.) are connected to a single central cable, like students in the classroom sitting along a single row. Data travels along this central cable, and all devices can hear the communication. An example of this is an older Ethernet network in an office, where all computers are connected to a single main cable.
Star Topology: Picture a hub or central point in a city where multiple roads meet. Each road leads to a different neighborhood. In a star topology, all devices are connected to a central hub, much like roads leading to a central point. All communication goes through this central hub. A common example is your home Wi-Fi network. All devices connect to the router at the center for communication.
Ring Topology: Visualize a group of friends sitting in a circle, passing a single note around. Each friend receives the note, reads it, and then passes it to the next friend. In a ring topology, devices are connected circularly, forming a loop. Data circulates this loop, passing through each device in the network until it reaches its destination. An example could be a token ring network, though this is less common now.
Mesh Topology: Think of a web of friends where everyone is directly connected to everyone else. In a mesh topology, every device is connected to every other device, creating a highly interconnected network. This setup provides redundancy and multiple paths for communication. An example could be the internet itself, where millions of servers and devices are connected, allowing data to take various routes.
Each of these topologies has its advantages and disadvantages. Bus and ring topologies can suffer from communication issues if the central cable or connection is disrupted. Star topology is easy to manage but depends on the central hub. Mesh topology offers robustness but can be complex to set up and maintain.
Network protocols and the OSI model 💡:
Network Protocols: Network protocols are like languages that computers use to communicate with each other over a network. Just like people use languages like English, Spanish, or French to understand each other, computers use protocols to exchange information.
Imagine you and a friend are sending messages back and forth. Before you start, you both agree to use a specific set of rules. For example, you might say, "Let's send messages in English, and we'll start every message with 'Hi' and end with 'Bye'." This agreement on rules is similar to how computers follow protocols.
Example: Think of sending an email. When you hit the "Send" button, your email application uses the SMTP (Simple Mail Transfer Protocol) to send your message to the email server. The email server then uses POP3 or IMAP protocols to receive and store your email until the recipient fetches it. These protocols ensure that your email gets from your computer to the recipient's computer in a structured and understandable way.
The OSI Model: The OSI (Open Systems Interconnection) model is a way to understand how different parts of network communication work together. It's like a blueprint that breaks down the communication process into layers, each with a specific role.
Imagine you're sending a package through a series of checkpoints. Each checkpoint has a specific task, like checking the address, making sure the package is secure, and so on. The OSI model's layers work similarly to make sure data travels smoothly through a network.
Example: Let's say you're watching a YouTube video. Here's how the OSI model's layers might relate to this:
Physical Layer: This is like the actual cables and hardware that transmit data. It's like the road the package delivery trucks use. In the YouTube example, it's the actual physical cables and Wi-Fi signals that carry the video data.
Data Link Layer: This layer makes sure the data is error-free as it travels. It's like the checkpoints where the package's contents are verified before moving to the next checkpoint. In our YouTube scenario, this layer ensures that the video data is accurately transmitted without any errors.
Network Layer: This layer handles routing, like deciding the best path for your data to travel. It's similar to the maps that delivery trucks use to find the shortest route. In the YouTube case, this layer ensures that the video data takes the best path through the network to reach your device.
Transport Layer: This layer manages the actual sending and receiving of data between your device and the server. It's like the delivery trucks that transport the package. For YouTube, this layer makes sure that the video data packets are sent and received in the correct order.
Session Layer: This layer manages the session between your device and the server. It's like the communication between the package sender and receiver. In the YouTube example, this layer maintains the connection while you're watching the video.
Presentation Layer: This layer helps with data translation and encryption. It's like translating the package instructions into the local language at each checkpoint. In the context of YouTube, this layer might handle the video compression and encryption.
Application Layer: This is the layer you interact with directly. It's like the package sender preparing the package and the receiver opening it. In the YouTube case, it's the actual application or service you're using to watch the video.
Remember, the OSI model's layers work together to ensure that data is transmitted correctly and efficiently across a network, just like how the checkpoints and processes ensure your package gets delivered intact.
Module 2: Networking Devices and Media 🚀
🌐 Network devices: 🌐 Router, 🔄 Switch, 🌀 Hub, 📶 Modem
Let's break down these network devices using examples:
🌐 Router: A router is like the traffic cop for your network. It connects different devices to the internet and manages the flow of data between them. Just as a traffic cop directs cars on different roads, a router directs data to the right devices. It helps create a local network at your home or office and connects it to the larger internet world.
Real-world example: Imagine your home as a neighborhood, and the router is like the central intersection where all the roads (devices) meet. It makes sure that data, like web pages or videos, gets to the right device, like your phone or laptop.
🔄 Switch: A switch is like a smart connector. It connects devices within a local network, like your home network. It's smarter than a hub (we'll talk about that next) because it knows which device is where. When one device wants to talk to another, the switch makes sure the message goes only to the intended device.
Real-world example: Think of a switch as a mailbox area in an apartment building. Each mailbox represents a device. When someone drops a letter (data) in the mailbox, the apartment building's system (switch) ensures that the letter goes to the right mailbox and not to all mailboxes.
🌀 Hub: A hub is like a loudspeaker that broadcasts messages to all devices connected to it. It's not very smart – when one device sends data, the hub sends it to all connected devices, whether they need it or not. This can create unnecessary network traffic.
Real-world example: A hub is like a megaphone in a park. When someone speaks into the megaphone, everyone in the park can hear the message, even if it's only meant for one person.
📶 Modem: A modem is like a translator between your home devices and the language of the internet service provider (ISP). It converts the digital data from your devices into a format that can travel over the ISP's network, and vice versa.
Real-world example: Imagine you're sending a letter to a friend in a different country. The modem is like the translator who converts your letter into the language your friend understands and also translates their replies back into a language you can understand.
Remember, these devices work together to keep your network running smoothly, just like a team effort!
🔌 Network cables and connectors: 🌐 Ethernet, 🔮 Fiber optics
Let's break down network cables and connectors using examples:
🌐 Ethernet Cables and Connectors:
Imagine Ethernet cables as the roads that allow information to travel between different devices, like your computer, gaming console, or smart TV, and the internet router. These cables have connectors at the ends that plug into devices.
Ethernet cables are like the pathways in a neighborhood. Just like cars use roads to move around the neighborhood, your devices use Ethernet cables to send and receive data. The connectors are like the entry and exit ramps that connect the roads to your driveway (devices) and the main street (router).
For instance, when you watch a video on YouTube, the video data travels from the internet to your router, and then it uses the Ethernet cables to reach your computer. This way, you can enjoy smooth videos and online games.
🔮 Fiber Optic Cables and Connectors:
Fiber optic cables are like super-fast highways for data. Imagine them as special tunnels made of glass or plastic that allow information to travel using light signals. Just as light passes through a window, data travels through these cables.
Think of fiber optic connectors as the doors that open and close to connect these cables to devices. They ensure the data can go in and out smoothly.
For example, imagine you're sending a big presentation to a colleague who's far away. Instead of using regular roads (copper cables), your data takes the super-fast fiber optic highway. It travels at incredible speeds, like a beam of light, reaching your colleague's computer in a blink. This is why fiber optics are used for things that need to be fast, like online video conferences with no lag.
In summary, Ethernet cables are like regular roads for data, while fiber optic cables are like super-speed highways. Both use connectors to link devices and make sure data travels seamlessly, whether it's a video or an important work file.
📡 Wireless technologies: 📶 Wi-Fi, 🦷 Bluetooth
Let's break down network cables and connectors using examples:
📶 Wi-Fi (Wireless Fidelity): Imagine Wi-Fi as a way for your devices, like phones, tablets, and computers, to talk to each other without using any wires. It's like magic internet that's floating all around you. You can think of it as a super fast invisible thread that connects your devices to the internet and lets them share information.
Real-time Example: Remember when you connect your phone to your home Wi-Fi network? It's like giving your phone a secret code to talk to your router. Once they're connected, your phone can use the internet without any physical cables.
🦷 Bluetooth: Bluetooth is like a digital handshake between devices. It's a way for gadgets to chat with each other over short distances, usually less than 30 feet. It's like a tiny radio station that devices tune into so they can share stuff.
Real-time Example: Think about wireless headphones or earbuds. When you connect them to your phone using Bluetooth, it's like they're having a private conversation. Your phone sends music or podcasts to your headphones through Bluetooth without any cords getting in the way.
In a nutshell, Wi-Fi lets devices connect to the internet without wires, while Bluetooth lets devices share things when they're close. They're both part of the wireless technology family, making our devices more convenient and fun to use! 🌐🎧
🌐 Network Fundamentals:
Module 3: IP Addressing and Subnetting
IPv4 (Internet Protocol version 4):
Think of IPv4 as a system that gives unique addresses to devices (like computers, phones, and servers) on the internet so they can communicate with each other.
Real-Time Example:
Imagine you're sending letters to your friends all over the world. Each friend lives in a different house, and you need their address to make sure your letters reach them. Similarly, in computer networking, devices need unique addresses to send and receive data over the internet.
In the world of networking, every device (like your computer or smartphone) is assigned an IPv4 address, which looks something like this: 192.168.1.1. This address is like your friend's house address, but for your device on the internet.
Now, let's say you want to visit a website, like www.example.com. Just like you need your friend's address to send them a letter, your device needs the website's address to connect to it. Websites also have their own unique IPv4 addresses, like 203.0.113.10.
So, when you type "www.example.com" in your web browser and hit Enter, your device uses the Domain Name System (DNS) to find the website's IPv4 address (203.0.113.10). It's like looking up your friend's address in a phone book.
Once your device knows the website's IPv4 address, it can send a request to that address, asking for the website's content. The website's server receives your request and sends back the requested content, like the webpage you wanted to see.
In summary, IPv4 is like a global addressing system for devices on the internet. It helps devices find each other, just like addresses help you find your friends' houses. This system allows you to access websites, send emails, stream videos, and do many other things on the internet!
However, it's important to note that IPv4 addresses are running out due to the increasing number of devices connected to the internet. This led to the development of IPv6, which provides a much larger pool of addresses to accommodate the growing demand.
IPv6 (Internet Protocol version 6) :
Imagine you're a postal worker, and your job is to deliver mail to houses in a neighborhood. Each house has a unique address so you know exactly where to deliver the mail. In the world of computer networking, devices like computers, smartphones, and servers also need unique addresses to communicate with each other over the internet. This is where IPv6 comes into play.
IPv6 (Internet Protocol version 6) is like a new and improved system for giving addresses to devices on the internet. Just like the postal system needs more addresses as more houses are built, the internet needs more addresses as more devices connect to it.
In the past, we used IPv4, which is like having a limited set of addresses. It's a bit like if you only had a hundred addresses to cover the entire world. But with so many devices nowadays – phones, laptops, smart TVs, and even smart fridges – we're running out of addresses. That's where IPv6 comes in, giving us a practically unlimited number of addresses.
Think of IPv6 addresses as really long strings of numbers and letters. They look like this: 2001:0db8:85a3:0000:0000:8a2e:0370:7334. These long addresses help make sure every device can have its unique identifier.
Here's the real-time example: Imagine you want to visit a website. Your device (let's call it Device A) needs to connect to the web server (Device B) that hosts the website. With IPv6, Device A and Device B each have their own unique IPv6 address.
When you type the website's address into your browser, your device (Device A) uses its IPv6 address to find the right path to the web server (Device B) hosting the website. It's a bit like writing down the specific address of the house you want to visit, but in this case, it's a digital address.
With all these unique IPv6 addresses, the internet can handle the growing number of devices and services without running out of room. It's like having an almost infinite number of addresses for all the devices to play nicely and communicate with each other.
In summary, IPv6 is like a super-expanded address system for devices on the internet. It ensures that as more and more devices join the online world, there are enough unique addresses for everyone, just like houses on a street. This way, your devices can talk to each other and access websites without any address shortage issues.
Difference between IPv4 IPv6 🌍 :
IPv4 (Internet Protocol version 4): Imagine the internet as a gigantic neighborhood where each house has a unique address, just like in the real world. In IPv4, these addresses are like phone numbers for computers. However, there's a limitation with IPv4 – it only has a limited number of unique addresses (about 4.3 billion). Just like having only a certain number of phone numbers available in an area code, this can cause problems as more and more devices want to connect to the internet.
Example: Think of it like a town where houses are computers. If each house has a unique address, there's a limit to the number of houses you can have in that town. Eventually, if you need more houses, you'll run out of addresses.
IPv6 (Internet Protocol version 6): Now, imagine a new town with a much bigger addressing system. IPv6 is like that – it's a new protocol that allows for a practically limitless number of unique addresses. This is important because in the real world, we're not just connecting computers and phones anymore; we're connecting cars, smart fridges, thermostats, and all sorts of devices.
Example: Imagine a city with addresses that aren't just numbers but also include letters. This would allow for way more unique addresses. So, even if the city grows and more devices (houses) are added, there will still be plenty of unique addresses available.
In computer networking terms:
IPv4 addresses are 32-bit long and expressed in four groups of numbers separated by periods (e.g., 192.168.1.1).
IPv6 addresses are 128-bit long and are written in groups of hexadecimal digits separated by colons (e.g., 2001:0db8:85a3:0000:0000:8a2e:0370:7334).
In summary, IPv4 had a limited number of addresses, which was fine when the internet was small, but it caused issues as the internet grew. IPv6 was introduced to solve this problem by providing a much larger pool of unique addresses, allowing for the growth of the Internet of Things (IoT) and all the devices we connect to the Internet today.
IP Address Classes 🏠:
Imagine you're sending mail to different houses in a neighbourhood. Each house has a unique address so the mail carrier can find it. Similarly, in computer networking, devices on a network like computers, smartphones, and servers have unique addresses called IP addresses. These IP addresses help data find its way to the right device on the network.
IP addresses are divided into classes, which are like different categories of addresses based on the size of the network they're used for. There used to be five classes (A, B, C, D, and E), but now we mostly use classless addressing with CIDR (Classless Inter-Domain Routing). Still, it's good to know the basics of the old classes.
Class A Address:
Imagine a huge apartment building with thousands of apartments. Each apartment has its number, but the building itself has only one street address. In networking terms, a Class A IP address is like this big apartment building. The first part of the IP address identifies the network, and the rest is used for devices within that network.
Example: 10.0.0.1 Here, 10 is the network part, and 0.0.1 is the device part.
Class B Address:
Now, think of a street with several medium-sized houses. Each house has its number, and the street is divided into blocks. In networking, a Class B IP address is like this street. The first two parts of the IP address identify the network, and the other two parts are for devices.
Example: 172.16.0.1 Here, 172.16 is the network part, and 0.1 is the device part.
Class C Address:
Imagine a suburban neighborhood with many small houses. Each house has its unique number, and the neighborhood is divided into different sections. In networking, a Class C IP address is like this neighborhood. The first three parts of the IP address are for the network, and the last part is for devices.
Example: 192.168.1.1 Here, 192.168.1 is the network part, and 1 is the device part.
These classes helped organize IP addresses based on the size of the network, but they had limitations. For instance, Class A addresses were in short supply because they could create massive networks.
Today, CIDR is used, allowing more flexible allocation of addresses. This method doesn't strictly follow the old class divisions, making it easier to manage addresses and efficiently use them.
Subnetting and CIDR Notation 🔢:
Subnetting: Imagine you have a big house with many rooms, and you want to organize the rooms into smaller sections to manage them more effectively. Subnetting is like dividing your house into sections. In computer networking, it's the process of breaking down a larger network into smaller, more manageable sub-networks (subnets).
Example: Let's say you have a network with IP address range 192.168.1.0 to 192.168.1.255. That's a big network with 256 possible addresses. Now, you want to divide this network into smaller chunks for different departments in your organization. You decide to create two subnets: one for the Sales team and one for the IT team.
You could subnet it like this:
Sales subnet: 192.168.1.0 to 192.168.1.127 (addresses 0 to 127)
IT subnet: 192.168.1.128 to 192.168.1.255 (addresses 128 to 255)
This way, you've divided your network into two smaller sections to better manage the devices and traffic for each department.
CIDR Notation: CIDR stands for Classless Inter-Domain Routing. It's a way of representing IP addresses and their associated routing prefix. It's more efficient than the older classful addressing because it allows for flexible allocation of address space.
Example: In CIDR notation, an IP address is followed by a slash and a number, like this: IP_address/prefix_length. The prefix length indicates how many bits in the IP address are used for the network part.
If you have an IP address 192.168.1.0 with a subnet mask of 255.255.255.128 (which means the first 25 bits are for the network and the last 7 bits are for hosts), you can represent it in CIDR notation as 192.168.1.0/25.
This means the first 25 bits of the IP address represent the network, and you have 7 bits left for hosts. So, you have a subnet that includes IP addresses from 192.168.1.0 to 192.168.1.127.
In summary, subnetting is about breaking down large networks into smaller parts for better management, and CIDR notation is a concise way of representing these subdivisions in terms of IP addresses and their associated prefixes.
🌐 Module 4: Networking Protocols 🌐
Networking Protocols:
Think of networking protocols as a set of rules that devices use to communicate with each other over a network. Just like people follow specific social norms to have meaningful conversations, devices need protocols to ensure they can understand and exchange data effectively.
Example: Sending a Letter
Imagine you want to send a letter to a friend. To make sure your message reaches them accurately, you follow certain steps:
Addressing: You write your friend's address and your address on the envelope.
Posting: You take the letter to the post office. The post office handles the routing and delivery of your letter based on the addresses.
Delivery: The letter reaches your friend's mailbox, and they can read your message.
In this example, the process of sending the letter involves a set of steps and rules that ensure successful communication. Similarly, in the world of computers and networks, we have protocols that devices follow to communicate effectively.
Example: HTTP Protocol
One commonly used protocol is HTTP (Hypertext Transfer Protocol). It's like the language that web browsers (like Chrome or Firefox) and web servers (where websites are stored) use to talk to each other.
Imagine you want to visit a website. Here's what happens:
Request: You type a website's address (URL) in your browser and hit Enter.
HTTP Request: Your browser sends an HTTP request to the web server asking for the website's content.
Processing: The web server receives your request, processes it, and gathers the requested information.
HTTP Response: The web server sends back an HTTP response with the website's content (text, images, videos, etc.).
Display: Your browser receives the response, interprets it, and displays the website on your screen.
HTTP is the "language" that makes sure your browser and the web server understand each other. Just like your letter had an address and a format, HTTP requests and responses follow a specific structure so that information can be properly exchanged.
🌐 TCP/IP protocol suite 🌐 :
🌐 TCP/IP Protocol Suite Explained Simply 🌐
The TCP/IP protocol suite is like a set of rules that computers use to communicate with each other over the internet. Just like people follow certain manners when talking to each other, computers follow these rules to exchange information.
Think of it as sending a letter to your friend using a postal service:
Addressing: You put your friend's address as the destination on the envelope. Similarly, in TCP/IP, each computer has an IP address, which is like its unique postal address on the internet.
Dividing Content: You write your letter and divide it into paragraphs. In TCP/IP, your message is divided into smaller chunks called packets. Each packet contains a part of your message along with information about where it's coming from and where it's going.
Sending and Receiving: You send the envelopes containing paragraphs of your letter. Similarly, packets are sent from your computer to the destination computer over the internet.
Reassembling: Your friend receives the envelopes, opens them, and puts the paragraphs together to read your full letter. In TCP/IP, the destination computer receives the packets and reassembles them in the correct order to recreate your original message.
Confirmation: Your friend sends you a note saying they got your letter. In TCP/IP, after receiving each packet, the destination computer sends a message back to the sender, confirming that it got the packet. If the sender doesn't receive confirmation, it knows to resend that packet.
Now, let's add a example using a web page request:
Imagine you're using your web browser to visit a website:
Addressing: You type the website's address (URL) in the browser. This is like putting your friend's address on the envelope.
Dividing Content: The webpage you want to see is divided into packets. Each packet contains a part of the webpage content.
Sending and Receiving: Your computer sends these packets to the web server where the website is hosted.
Reassembling: The server receives the packets and reassembles them to create the complete webpage.
Confirmation: The server sends back the requested webpage, divided into packets again. Your computer receives and reassembles them to display the webpage on your screen.
Just like that, the TCP/IP protocol suite ensures that information flows smoothly across the internet, just as your letters find their way to your friend's house using postal services.
I hope this example helps you understand the 🌐 TCP/IP protocol suite 🌐 better! If you have more questions or need further explanations, feel free to ask. 🚀
🌐 HTTP, HTTPS, FTP, SMTP, POP3, IMAP 🌐 :
HTTP (Hypertext Transfer Protocol): HTTP is the protocol that powers the web. It's used for transferring data (usually in the form of web pages) between a web server and a web browser. When you type a URL into your browser's address bar and hit Enter, your browser sends an HTTP request to the server, and the server responds with the requested webpage. For example, when you visit "http://www.example.com," your browser is using HTTP to fetch and display the webpage.
HTTPS (Hypertext Transfer Protocol Secure): HTTPS is a secure version of HTTP. It uses encryption to protect the data being transferred between your browser and the web server. This is important for sensitive information like passwords and credit card details. When you see a little padlock icon in your browser's address bar and a URL starting with "https://," it means you're using HTTPS. Online shopping sites often use HTTPS to ensure your payment details are secure.
FTP (File Transfer Protocol): FTP is a way to transfer files between computers over a network. It's commonly used for uploading and downloading files to and from a remote server. Imagine you're a web developer and you need to upload a new version of your website to a web server. You can use FTP to transfer your website's files from your computer to the server.
SMTP (Simple Mail Transfer Protocol): SMTP is the protocol used to send emails. When you compose an email and hit "Send," your email client (like Gmail or Outlook) uses SMTP to send the email to the recipient's email server. Think of it as the digital postman that delivers your emails. For instance, when you send an email to a friend, SMTP is the protocol responsible for sending it from your mailbox to theirs.
POP3 (Post Office Protocol 3) and IMAP (Internet Message Access Protocol): POP3 and IMAP are protocols used to retrieve emails from a mail server to your email client. POP3 downloads emails to your device, removing them from the server. IMAP, on the other hand, keeps emails on the server and syncs them with your email client. Think of POP3 as taking letters from a post office to keep at home, while IMAP is like having a remote mailbox that you access from different places.
🌐 DNS (Domain Name System) 🌐 :
The Domain Name System (DNS) is like the phonebook of the internet. It's a system that translates human-friendly domain names, like "www.example.com," into IP addresses, which are the unique numerical addresses that computers use to identify each other on the internet.
Imagine you want to visit a website, let's say "www.google.com." Instead of typing in its IP address (which is a series of numbers like 216.58.216.164), you simply type the domain name in your browser's address bar. Here's how DNS works with a real-time example:
Step 1: You type in a URL You open your web browser and type in "www.google.com" to search for something.
Step 2: Your Computer Checks Its Cache Your computer checks if it already knows the IP address of "www.google.com" from previous visits. If it does, great! It doesn't need to do anything else.
Step 3: Your Computer Asks the Recursive DNS Server If your computer doesn't have the IP address, it asks a Recursive DNS Server. Think of this server like an internet detective. It might not know the answer itself, but it's determined to find it!
Step 4: Recursive DNS Server Investigates The Recursive DNS Server might have to ask other DNS servers to find the answer. It's like asking multiple people for directions to a place.
Step 5: Recursive DNS Server Finds the Answer Eventually, the Recursive DNS Server finds the IP address for "www.google.com" and sends it back to your computer.
Step 6: Your Computer Stores the Answer Your computer stores the IP address in its cache so it doesn't have to go through this process again the next time you visit the same website.
Step 7: You Reach the Website Armed with the IP address, your computer sends a request to the IP address, and you're connected to the Google website.
So, in simple terms, DNS makes it easier for us to use human-readable domain names to access websites, while behind the scenes, it translates them into the numeric IP addresses that computers use to communicate on the internet.
Next time you browse the web, remember that the DNS is the one helping you navigate by converting names into numbers! 🌐🔍
🌐 DHCP (Dynamic Host Configuration Protocol) 🌐 :
What is DHCP?
Imagine you have a bunch of devices like computers, smartphones, and smart TVs at home that need to connect to the internet. Each of these devices needs a unique address on the network so that data can be sent to and received from them correctly. This is similar to how houses have unique street addresses.
Now, manually giving an address to each device can be time-consuming and prone to mistakes. That's where DHCP comes in! DHCP is like a helpful system that automatically assigns and manages addresses for all your devices on the network.
Example: Think of your home as a big network, and each device in your home as a house on that network. When a new device joins the network, it needs an address to communicate with other devices and access the internet. Here's how DHCP works in this scenario:
New Device Wants to Join: Imagine you just got a new smartphone and want to connect it to your home Wi-Fi.
Device Sends a Request: When you turn on your smartphone's Wi-Fi, it sends a special request to the network saying, "Hey, I need an address so I can be part of the network."
DHCP Server Responds: In your home, there's a device called a DHCP server (it could be your router). This server is like a manager that hands out addresses. It gets the request from your smartphone and says, "Sure! Here's an address for you."
Device Gets an Address: Your smartphone receives an address from the DHCP server. This address is temporary and is called an "IP address." It's like the house number for your device on the network.
Device Can Now Communicate: With this assigned IP address, your smartphone can now talk to other devices on the network and access the internet. It's like your smartphone has a place to live in the big network neighborhood!
Lease Time: The DHCP server also gives your smartphone a "lease time," which is like how long your smartphone can stay at that address. After this time, your smartphone might need to renew its lease to keep using that address.
Network Architecture and Design 🌐
Module 5: Network Architecture 🏢
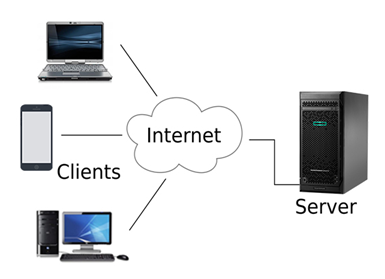
Network Architecture in computer networking refers to the way computer systems, devices, and components are organized and connected to enable communication and data exchange. It's like designing the layout and structure of a digital neighbourhood where devices can talk to each other
Client-server vs. Peer-to-peer models 📡🤝:
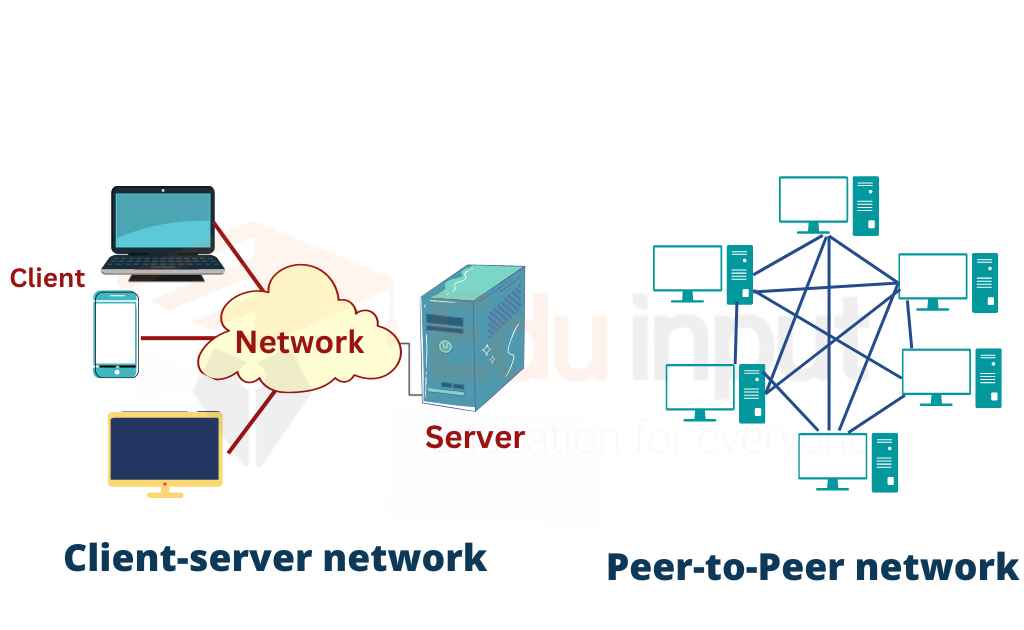
**
Client-Server Model** 📡🤝
In the client-server model of computer networking, devices are divided into two main roles: clients and servers. Clients are like customers who request services or resources, while servers are like service providers that fulfill those requests. This setup is similar to how you interact with a restaurant.
example: Think of a restaurant. You (the client) sit at a table and order food from the waiter (the server). The kitchen prepares your food and sends it to your table. Here, you're the client requesting a service (food) from the server (waiter and kitchen).
In computer networking:
Clients: Devices like your computer, phone, or tablet that ask for resources or services, like a web page or a file.
Servers: Powerful computers or systems that store and manage resources, providing services to clients. Examples are web servers hosting websites or file servers storing documents.
Peer-to-Peer Model 📡🤝
In the peer-to-peer (P2P) model, devices are equals that interact directly with each other. Each device can act as both a client and a server, sharing resources or information directly without relying on a central server. This is similar to a potluck gathering.
example: Imagine a potluck party. Everyone brings their dish to share with others. Each person can taste what others have brought, and you don't need a single host serving everything. Everyone contributes and benefits equally.
In computer networking:
Peers: Devices that are both clients and servers. They can request and provide resources to other peers.
No Central Server: Unlike the restaurant or client-server model, there's no central server mediating interactions. Devices communicate directly with each other.
Comparison:
Client-Server: Centralized, efficient for managing large amounts of clients, used for services like websites, email, and streaming platforms.
Peer-to-Peer: Decentralized, suitable for smaller networks, used for file sharing, collaboration tools, and some communication apps.
Both models have their strengths and weaknesses, and their choice depends on the specific needs of the network and its users. 📡🤝🌐
Network security considerations 🔒🔐
Network security considerations in computer networking involve protecting the information and resources within a network from unauthorized access, attacks, and other threats. Think of it as setting up locks and guards to keep unwanted visitors out of your digital space.
Real-time example: Imagine your network as a fortress that needs protection:
User Authentication: Just like a guard at the entrance checks IDs, networks use usernames and passwords to ensure only authorized users can access resources. For instance, when you log in to your email account, you need to provide your username and password.
Firewalls: Think of a firewall as a moat around the fortress. It filters incoming and outgoing traffic, allowing only safe data to pass through. It prevents unauthorized access and blocks malicious attempts, like a virtual security guard.
Encryption: Imagine sending secret messages written in code that only the intended recipient can decipher. In networks, encryption converts data into a code that can only be understood by those who have the decryption key. This keeps sensitive information, like credit card details during online shopping, safe from hackers.
Antivirus Software: Think of this as a patrol team within the fortress. It scans files and programs for harmful code (viruses, malware) and removes or quarantines them to prevent infection.
Updates and Patches: Just like fixing weak spots in the fortress wall, software updates and patches fix vulnerabilities in network systems. Regularly updating your devices and software helps keep hackers from exploiting known weaknesses.
Access Control: Imagine giving specific keys to different rooms in the fortress. Similarly, access control ensures that users can only access resources they're authorized to. This prevents someone from accessing sensitive areas or information they shouldn't have.
Intrusion Detection System (IDS): This is like a motion sensor within the fortress. It watches for unusual behavior or patterns that might indicate a security breach and alerts administrators so they can take action.
Backup and Redundancy: Think of this as making copies of important documents. Regular backups ensure that even if a breach or data loss occurs, you can restore your network to a previous safe state.
So, network security considerations involve setting up these layers of protection to keep your digital space safe from cyber threats, just like you would secure a fortress to keep it safe from intruders. 🔒🔐🏰
Scalability and redundancy 📈🔁
Scalability 📈
Scalability in computer networking refers to the ability of a network or system to handle a growing amount of work, users, or data without sacrificing performance. It's like designing a road system that can accommodate more and more cars without causing traffic jams.
example: Think of a social media platform. As more users join and post content, the platform should still load quickly and respond to actions like likes and comments. Scalability ensures that the network infrastructure and servers can handle the increased demand without slowing down.
Redundancy 🔁
Redundancy in computer networking involves having backup components or systems in place to prevent a single point of failure. It's like having spare tires in your car or extra ingredients in the kitchen in case something breaks or goes wrong.
example: Imagine an online shopping website. If the main server that hosts the website crashes, customers won't be able to access it. But with redundancy, there could be multiple servers hosting the same website simultaneously. If one server fails, the traffic is automatically directed to the other servers, ensuring the website remains accessible.
In simpler terms:
Scalability is about making sure a network can handle more traffic and users as the demand grows, just like expanding a highway to accommodate more cars.
Redundancy is like having backup plans or spare parts to keep things running smoothly, similar to having extra batteries for your flashlight in case the first one runs out.
Both scalability and redundancy ensure that computer networks are adaptable, reliable, and can withstand unexpected challenges. 📈🔁🌐
Module 6: Network Design 🌐

Network design refers to the process of planning and creating a network that connects computers, devices, and resources together in an efficient and reliable way. It's like designing a road system for data to travel on, ensuring that information reaches its destination quickly and smoothly.
Imagine you're setting up a new office space with multiple rooms. Each room needs to have electricity, water, and internet connections. Network design is like figuring out the best way to lay down the wiring and pipes so that every room gets the services it needs without any interruptions.
In the same way, when you're creating a network for a business, school, or even your home, you need to consider things like:
Layout: Just as you'd plan where to place rooms and hallways, you'll decide how computers and devices connect to each other.
Traffic Flow: Similar to arranging roads to avoid traffic jams, you'll organize the network to prevent data congestion and slowdowns.
Redundancy: Like having backup power sources, you'll create duplicate paths for data in case one route fails, ensuring uninterrupted connectivity.
Security: Just as you'd lock certain rooms to protect valuables, you'll implement measures to safeguard sensitive information from unauthorized access.
Scalability: If you plan to expand your office in the future, you'll design the network to easily accommodate more devices without major overhauls.
For instance, consider a school network: Teachers need to access educational resources, students need to submit assignments, and administrators need to manage records. A well-designed network ensures that all these tasks happen smoothly. If the network is poorly designed, it might result in slow internet, lost assignments, or security breaches.
In simple terms, network design is like creating an organized roadmap for data to travel, making sure it reaches the right destinations efficiently, securely, and with room to grow.
Network design principles 🛠️:
Network design principles are guidelines and strategies that help in creating efficient and effective computer networks. These principles ensure that networks are reliable, scalable, secure, and capable of meeting the needs of their users. Think of network design principles as the blueprint for constructing a well-organized and functional network, much like planning the layout of a city.
1. Scalability: Just like a road system that can handle more traffic as a city grows, a network should be designed to handle increasing amounts of data and users. For instance, when a company expands and hires more employees, the network should be able to accommodate the additional devices and traffic without slowing down.
2. Redundancy: This is like having multiple routes to reach a destination. Having backup components and connections ensures that if one part of the network fails, there's an alternative path to keep things running smoothly. Think of it as having spare tires in case one goes flat.
3. Security: Network design should incorporate measures to protect data from unauthorized access. This is akin to having security guards at various entry points to a building. For example, a company's network might have firewalls, encryption, and authentication protocols to safeguard sensitive information.
4. Performance Optimization: Just as optimizing traffic signals can reduce congestion, network design aims to optimize the flow of data. This involves strategically placing devices like routers and switches to minimize delays and bottlenecks.
5. Flexibility: A network should be adaptable to changing needs, much like a flexible building layout that can be reconfigured for different purposes. For example, a university's network should be able to handle different types of users, from students to faculty, with varying requirements.
6. Cost-effectiveness: Designing a network is like planning a budget for a project. It's important to balance performance and capabilities with the available resources. For instance, a small business might not need the same level of complexity as a large corporation.
7. Ease of Management: Just as a city needs a central administration to manage various services, a network should be designed with simplicity in mind. This makes it easier to troubleshoot, monitor, and maintain the network infrastructure.
Imagine you're setting up a coffee shop. To follow network design principles:
Scalability: You set up a network that can handle more customers and devices as your coffee shop gains popularity.
Redundancy: You have two internet connections so that if one goes down, you can switch to the other without disrupting customer Wi-Fi.
Security: You set up a secure Wi-Fi password for customers and a separate network for your point-of-sale system to keep payment information safe.
Performance Optimization: You strategically place routers to ensure even coverage throughout the shop, preventing slow or dead zones.
Flexibility: You design the network so that you can easily add more devices or expand to a second location.
Cost-effectiveness: You balance the network's capabilities with your budget, opting for a suitable balance of performance and affordability.
Ease of Management: You organize the network setup in a way that even your non-technical staff can troubleshoot basic issues without much difficulty.
In essence, network design principles ensure that your network operates smoothly, adapts to changes, and meets the needs of your users, much like a well-planned city infrastructure.